Kemp invites you to download the Kemp Ansible module to try out in your organization to deliver an always-on application experience. Why? Because nearly every IT team within a firm is doing some level of automation and configuration management, with the latter being further adopted when DevOps plays a part. Ansible is one of the top-rated configuration management tools due to its simplicity and agentless architecture, becoming a must have tool for DevOps. Throughout this blog, I will outline the components that make up Kemp’s automation and configuration management strategy, as well as showcase how Ansible fits into this approach.
‘Kemp’s 360 central’ is the centralized management platform that crucially provides configuration management, visibility, control and licensing needed for your organization’s always-on application experience.

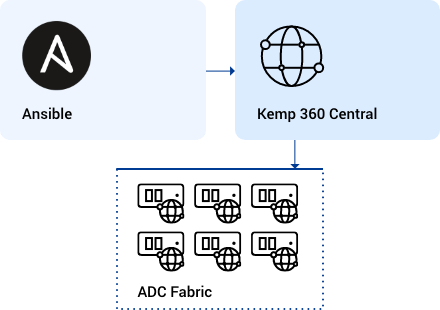
Ansible Module
Shown on the right of the image above, are all of the Kemp LoadMasters that are managed under ‘Kemp 360 Central.’ The Ansible module communicates directly with configuration management components of ‘Kemp 360 Central’, which in turn orchestrates the changes to the downstream ADCs. This allows administrators and application owners the ability to automate all the changes in one place, rather than needing to interact with the individual ADCs that may be distributed across different data centers and Clouds.
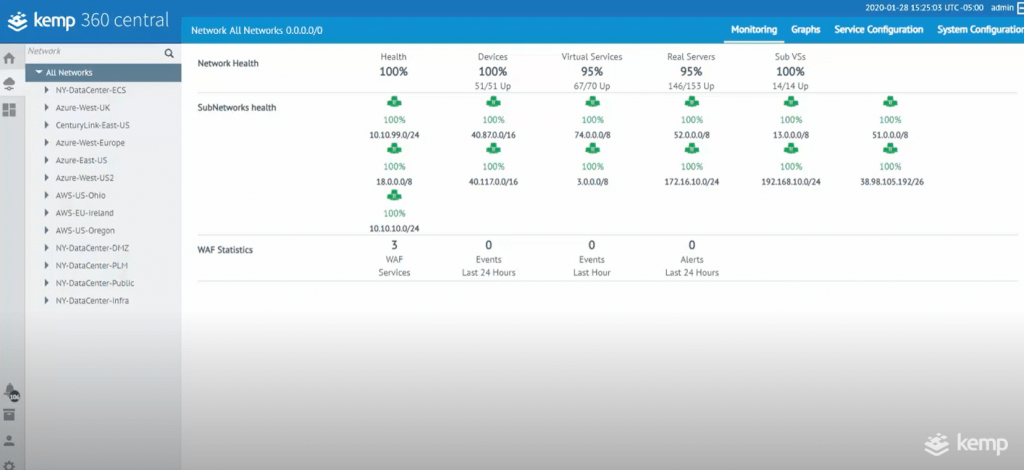
Above is a snapshot of how the Kemp 360 Central web interface will look. Several dozen load balancers are running and are distributed over multiple clouds and data centers. In the example shown, Kemp’s Metered Licensing is used, which drives that per app ADC model.
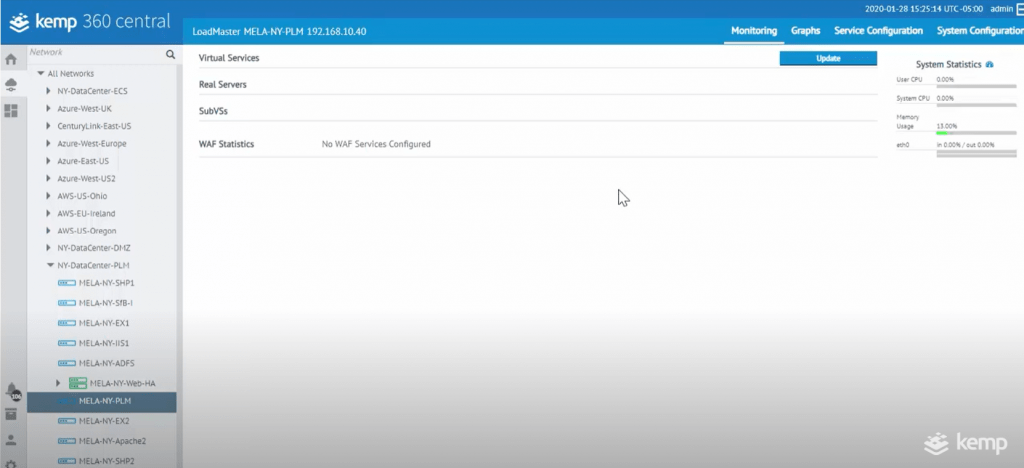
As the example shows, users will want to create a virtual service on a LoadMaster in their ‘New York Data Center.’ New applications will always need a new LoadMaster, and in this instance it is named ‘Mila NY PLM.’
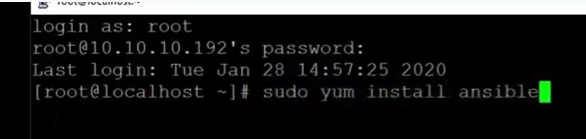
Using one of the sample Ansible playbooks Kemp provides, it will publish this application on port 443, alongside a clean install of CentOS 7. Ansible can then be installed, by using the ‘Sudo Yum’ install ansible command and typing Y, to start the process.
The Process
- Next up, install ‘Python requests,’ which is the Python HTTP library, and once again type Y to complete the installation. Once all of the components are installed, copy the Kemp Ansible module onto the system. The modules should already be downloaded from the Kemp system.
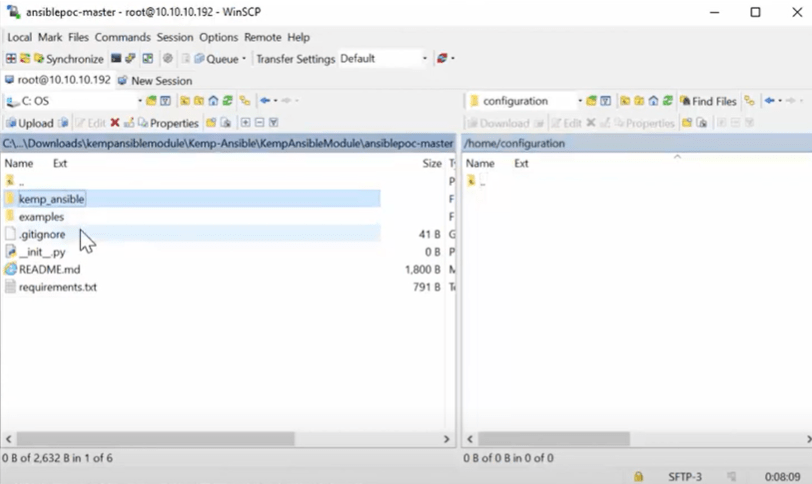
- The prior step being completed means the necessary directories cna transferred using ‘WinSPC.’ In this demonstration a directory was created at her home called ‘configuration,’ but feel free to copy them elsewhere, if you choose. (See below).
- Once Ansible is installed and the Kemp module is copied onto the system, a connection between the two needs to be provided in order for Ansible to know where to find the latter and run the playbooks. There are several ways to do this across the different Linux distributions, however in this example, we’re simply going to ‘modify profile’ to add those necessary export valuables, so they’re system wide.
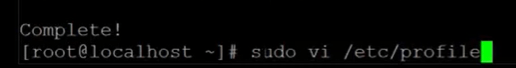
- Using ‘Sudo vi/ etc/ profile’, go ahead to the bottom, hit insert and enter two lines, then escape. Enter :WQto save it, followed by logging out and back in for this to take effect. Once complete, run export to confirm that they are listed.
- Now just edit the Ansible host file to allow the running of the playbooks on the local host, by typing ‘# sudi vi/ etc/ profile.’
- Once again, scroll to the bottom and hit insert, then type [local host]. Directly underneath that, type the IP address of this machine.
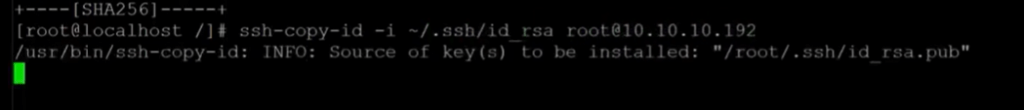
- The final step is to generate SSH keys to allow ansible to run the playbooks. Without taking this step, an error will be generated stating ‘failure to connect to SSH.’
- Go ahead and type, ‘SSH- keygen,’ and accept the defaults. Once that completes, use the SSH- copy- ID command to install the keys. Type yes, and provide the root password for the system.
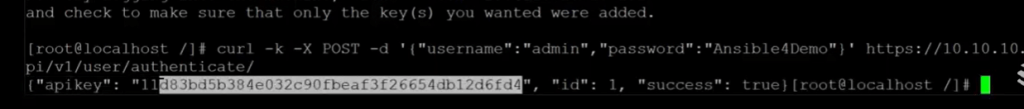
- After all of the prerequisites have been installed, we can start with the Ansible playbook. In order to run this playbook, ‘Kemp 360 Central’ needs to be authenticated. In order to do this, an API key needs to be obtained. Using curl, run the following command (see below), providing the admin credentials to get access to this key. Go ahead and copy out this to use in the playbook:
- Now, simply change the directory to the aforementioned ‘/home/configuration,’ where the sample playbooks are stored. Typing ‘LS,’ two samples will appear; a mediumConfig.yml, which includes some advanced configuration including content rules. As well as, a smallConfig.yml, which will just create a virtual service and some real servers. Since the example shown is relatively simple, consisting of a single virtual service and some real servers, the smallConfig.yml, would be best suited to modify it for this environment.
- The .yml file is broken up into a few different sections. At the top, we’re able to identify where to run the playbook, and in this case, it was ran locally, using that local host created in the host file earlier.
- Next, is where the variables can be modified that are used in this playbook, for this environment. So long as you provide the ‘Kemp 360 Central’ IP address, username, the API key that was generated earlier along with the details of the LoadMaster that we are seeking to modify.
- Last on the to-do list, are the tasks that are going to be ran using the variables provided. You are able to modify one, or all of these to get the results you want in the playbook.
- Go ahead and save the .yml file, and alongside this run ‘ansible-playbook,’ and specify the .yml file name.
- Without a doubt, everything should connect and run successfully. Now, go all the way back to the ‘Mila NY PML,’ or whichever you named it and refresh to see the newly added virtual service and real server listed.
Additional Information
As application development teams in many organizations are taking more ownership of business-critical applications, the DevOps team can share some responsibilities such as application publishing and service configuration. Different teams throughout an organization are using the same unified toolchain so there is no need to worry about lack of skill set. Kemp has developed an Ansible module to extend the configuration management capabilities to support Kemp’s customers application delivery environment. Many organizations have already adopted Kemp’s per-app Application Delivery Controller (ADC) model so there is no risk for these application development teams to impact other parts of the business.
